Why Cybersecurity Defines the Success of Digital Transformation
When organizations commit to digital transformation, the conversation is usually full of ambition: faster operations, more automation, cloud scale, connected ecosystems. But the reality is that none of these gains hold unless the foundation is secure. Cybersecurity is no longer simply a protective perimeter; it has become a fundamental determinant of whether transformation delivers meaningful, long-lasting results.
To understand this properly, we must view cybersecurity not as a technical exercise but as a set of outcomes the business actually needs: minimizing the impact of compromise, ensuring continuity even during an attack, and enabling teams to operate confidently in dynamic, interconnected environments. The challenge is that these objectives often get buried under technical jargon. Digital transformation only works when security becomes practical, contextual and aligned with how the business truly operates.
So the question becomes: how do organizations scope, develop and operate a security approach that fits the modern enterprise?
From Manual Defense to Intelligent Threat Detection
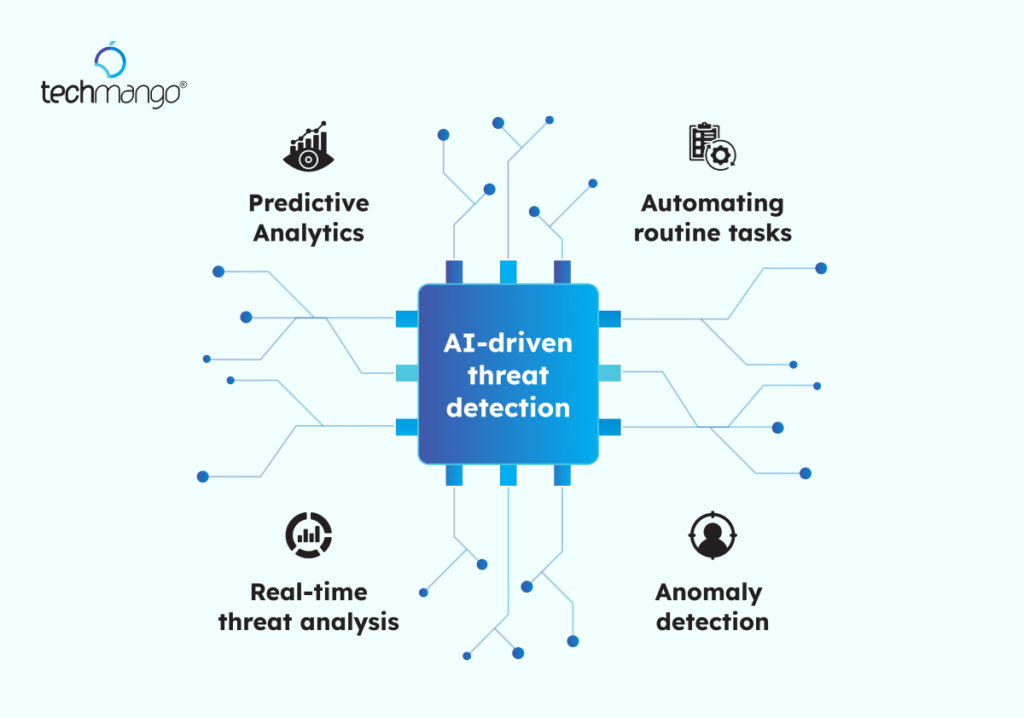
How can automated systems improve threat detection
Most organizations still rely on a security model built around manual review and reactive detection. Teams monitor dashboards, triage alerts and attempt to correlate incidents with limited context. While these approaches were sufficient in earlier eras, they struggle to match the speed and sophistication of modern threats.
Intelligent threat detection changes the equation by incorporating automation and machine reasoning. It continuously evaluates behaviors, correlates activity across systems and identifies patterns that humans are unlikely to spot at scale. This doesn’t replace human expertise but expands its reach. Analysts spend less time chasing false positives and more time strengthening defenses where it matters.
From a practical standpoint, intelligent detection gives enterprises a way to keep up with complexity rather than fall behind it.

Adopting a Zero-Trust Security Framework
What is zero trust and why is it needed
Zero trust can sound abstract—a collection of principles, identity checks and verification flows. But from an architectural point of view, it is simply a way of reducing the real-world consequences of compromise. Instead of assuming systems or users are safe because of where they are in the network, zero trust forces contextual decision-making. Access becomes based on identity, behavior, device posture and risk level.
To make this workable, organizations must start with context. What is the state of the business? Which systems are most sensitive? Which processes are essential for continuity? What patterns of collaboration, mobility or remote access must the security model support? An effective zero-trust program grows directly out of understanding these elements.
This approach isn’t theoretical—it is what allows modern enterprises to operate during mergers, cloud migrations and distributed work. Without the right starting context, zero trust becomes another framework on paper rather than a security philosophy that delivers.
How Leading Enterprises Are Enhancing Threat Detection Capabilities
How are companies improving cybersecurity
Organizations that make real progress in cybersecurity do so by grounding their improvements in operational reality, not technology alone. Several behaviors stand out:
- Integrating AI-driven analytics into SOC operations to create more accurate, contextual detections
- Strengthening identity-first controls such as conditional access and continuous verification
- Expanding telemetry across cloud, edge and on-prem systems to reduce blind spots
- Embedding security into DevOps practices rather than layering it on afterward
- Using threat intelligence to understand attacker behavior, not just isolated events
These initiatives enable security teams to shift from defensive firefighting to strategic risk reduction.
Challenges and Ethical Considerations in Modern Threat Detection
What are the challenges in using modern technologies for cybersecurity
It is easy to assume that AI-powered threat detection and zero trust will solve everything, but real transformation requires acknowledging several challenges:
Integration complexity
Most enterprises have a blend of legacy systems, cloud workloads and custom applications. Bringing them under a unified detection model requires thoughtful architecture.
Alert volume and false positives
Advanced tools can still overwhelm analysts unless tuned and contextualized properly.
Data privacy and oversight
Monitoring at scale must respect privacy laws, internal policies and employee trust.
Skills and adoption
Even high-quality tools fail when teams lack clarity on how to operate them day-to-day.
Addressing these challenges requires both technical planning and organizational change management.
Building a Resilient Cybersecurity Strategy with Techmango
Techmango helps enterprises shift from reactive protection to resilient, intelligence-driven security. Our approach is rooted in understanding business context first, then designing security capabilities that support those realities.
We support clients by:
- Implementing AI-powered threat detection systems that interpret patterns, behaviors and anomalies
- Designing and operationalizing zero-trust architectures tailored to hybrid and cloud environments
- Deploying continuous security controls that adapt as the organization evolves
- Integrating Generative AI services for automated incident analysis, documentation and response workflows
- Ensuring that identity, device, network and workload protections function cohesively
- Establishing governance structures that support long-term, measurable maturity
- Each engagement aligns with the client’s operational landscape, ensuring that security enhancements are both technically sound and practically deployable.
Conclusion: Securing the Future of Digital Transformation
Digital change changes the whole way a business works. But without smart security, it is easy for it to fall apart. Good cybersecurity, especially when it uses AI to spot threats and does not trust anyone by default, makes it less likely a business can be broken, puts security where it is needed most, and can keep a company safe for many years of digital change.
Those who take this path will be strong, run their work with confidence, and not fear innovation. Techmango is ready to help your business make a security system that makes sense for you, gets smarter all the time, and keeps up with the fast pace of digital growth.
Recent blogs
AI-powered Innovation: Reshaping the World of Mobile App Development
Frequently Asked Questions
How does AI improve cybersecurity in the digital transformation era?AI enhances cybersecurity by detecting anomalies, predicting potential threats, and automating responses. It continuously learns from data, identifying new attack patterns faster than traditional systems—helping organizations in Dubai and beyond protect digital assets in real time.
AI-driven threat detection uses machine learning and predictive analytics to identify and respond to cyber threats proactively. It reduces false positives, enables faster incident response, and ensures stronger protection against zero-day and advanced persistent threats (APTs).
How does AI support the Zero-Trust security model?AI enables Zero-Trust security by continuously analyzing user behavior, device identity, and contextual risk factors before granting access. It ensures granular access control and real-time monitoring, helping organizations enforce the principle of “never trust, always verify.”
What challenges do organizations face when adopting AI in cybersecurity?Common challenges include ensuring data privacy, mitigating algorithmic bias, and complying with regulations such as GDPR and CCPA. Businesses must implement governance frameworks and ethical AI practices to maintain security without compromising fairness or compliance.
Why choose Techmango for AI-powered cybersecurity solutions?Techmango delivers end-to-end AI-driven cybersecurity solutions using advanced frameworks like TensorFlow, PyTorch, Hadoop, and AWS. With expertise across data engineering and digital transformation, Techmango helps enterprises build resilient, scalable, and future-ready defense systems.